I am not normally a big fan of conspiracy theories, but I when I start to connect the dots on the evolution of DDoS, I can really only come to one conclusion that makes sense and holds together. You may be surprised at what I have found.
But first, my observations about DDoS.
We have all heard the stories about businesses getting hacked, bank accounts compromised, or credit cards stolen. These breaches happen quietly and discreetly, often only discovered long after the fact. I can clearly understand the motivation of a perpetrator behind this type of break in. They are looking to steal some information and sell it on the dark web.
On the other hand, a DDoS attack does not pose any security threat to a business’ data, or their bank accounts. It is used as a jamming tool to effectively cut off their communication by paralyzing their network. I have read vanilla articles detailing how extortion was the motivation. They generally assume the motive is money and DDoS attacks are monetized through extortion. You get attacked, your web site is down, and some dark figure contacts you via a back channel and offers to stop the attack for a ransom. Perhaps some DDoS attacks are motivated by this kind of extortion, but let’s dig a little deeper to see if there is a more plausible explanation.
Through my dealings with 100’s of IT people managing networks, almost all have experienced some sort of DDoS attack in the past 5 or 6 years.
To my knowledge, none of my contacts were ever approached by somebody attempting to extort money. When you think about this, taking a payment via extortion is a very risky endeavor for a criminal. The FBI could easily set up a sting at any time to track the payment. You would have to be very, very clever to extort and take payment and not get caught.
Another explanation is that many of these were revenge attacks from disgruntled employees or foreign agents. Maybe a few, but based on my sample and projecting it out, these DDoS attacks are widespread, and not just limited to key political targets. Businesses of all sizes have been affected, reaching into the millions. I can’t imagine that there are that many disgruntled customers or employees who all decided to settle their grievances with anonymous attacks in such a short time span. And what foreign agent would spend energy bringing down the Internet at a regional real estate office in Moline, Illinois? But it was happening and it was happening everywhere.
The real AHA moment came to me one day when I was having a beer with an IT reseller that sold high-end networking equipment. He reminisced about his 15 year run selling networking equipment with nice margins. Switches, Routers, Access Points.
But revenue was getting squeezed and had started to dry up by 2010. Instead of making $100K sales with $30K commission, many customers dumped their channel connection and started buying their equipment as a commodity on-line at much lower margins. There was very little incentive to work the sales channels with these diminishing returns. So what was a channel sales person going to do now to replace that lost income? The answer was this new market selling $200K integrated security systems and clearing $30K commission per sale.
I also learned after talking to several security consultants that it was rare to get a new customer willing to proactively purchase services unless they were required to by law. For example, the banking and financial industry had established some standards. But for large and medium private companies it is hard to extract $200K for a security system as a proactive purchase to protect against an event that had never happened.
I think you might be able to see where I am going with this, but it gets better!
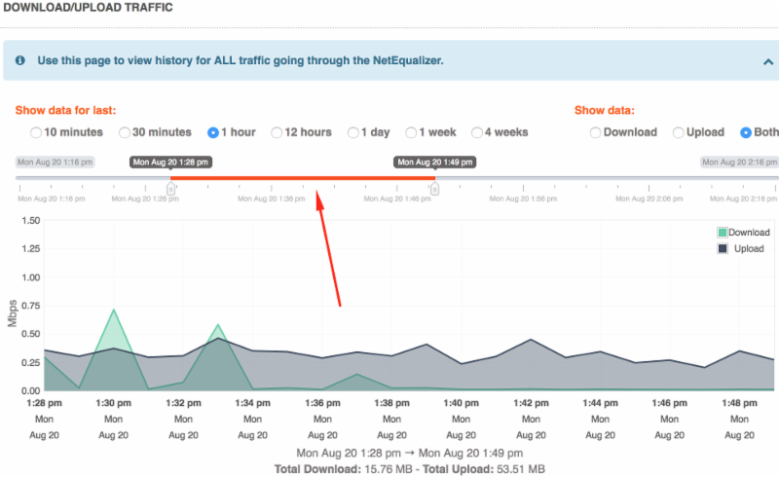
I also noticed that, post purchase of these rather pricey security systems, attacks would cease. The simple answer to this is that an on-site DDoS prevention tool generally has no chance of stopping a dedicated attack. A DDoS attack is done by thousands of hijacked home computers all hitting a business network from the outside. I have simulated them on my own network by having 100 virtual computers hitting our website over and over as fast as they can go and it cripples my web server.
The only way to stop the DDoS attack is at the source. In a real attack the victim must hunt down the source machine all the way back to their local ISP and have the ISP block the attacker at the source. Now imagine an attack coming from 1000 different sources located all over the world. For example, your home computer, if compromised by a hacker, could be taking part in an attack and you would never know it. Professional hackers have thousands of hijacked computers under their control (this is also how spammers work). The hacker turns your computer into a slave at its beck and call. And the hijacker is untraceable. When they initiate an attack they tell your computer to bombard a website of their choosing, along with the thousands of other computers in their control, and BAM! the website goes down.
So why do the attacks cease once a customer has purchased a security system? If the attacks continued after the purchase of the tool the customer would not be very happy with their purchase. My hypothesis: Basically, somebody is calling off the dogs once they get their money.
Let me know if you agree or disagree with my analysis and hypothesis. What do you think is happening?











Out of the Box Ideas for Security
February 19, 2021 — netequalizerI woke up this morning thinking about the IT industry and its shift from building infrastructure to an industry where everybody is tasked with security, a necessary evil that sucks the life out of companies that could be using their resources for revenue-generating projects. Every new grad I meet is getting their 1st job at one of many companies that provide various security services. From bank fraud investigation, white-night hacking, to security auditing, there must be 10’s if not 100’s of billions dollars being spent on these endeavors. Talk about a tax burden on society! The amount of money being spent on security and equipment is the real extortion, and there is no end in site.
The good news is , I have a few ideas that might help slow down this plague.
Immerse Your Real Data in Fake Data
Ever hear of the bank that keeps an exploding dye bag that they give to people who rob them? Why not apply the same concept to data. Create large fictitious databases and embed them within your real data. Obviously you will need a way internally to ignore the fake data and separate it from real data. Assume for a minute that this issue is easily differentiated by your internal systems. The fictitious financial data could then be traced when unscrupulous hacks try to use it. Worst case, it would create a waste of time for them.
Assuming the stolen data is sold on the dark web, their dark web customers are not going to be happy when they find out the data does not yield any nefarious benefits. The best case is this would also leave a trail for the good guys to figure out who stole the data just by monitoring these fictitious accounts. For example, John James Macintosh, Age 27, of Colby, Kansas does not exist, but his bank account does, and if somebody tried to access it you would instantly know to set a trap of some kind to locate the person accessing the account (if possible).
The same techniques are used in counter intelligence to root out traitors and spies. Carefully planted fake information is dispersed as classified, and by careful forensics security agencies can find the leaker (spy).
Keep the Scammers on the Phone
For spam and phone scams you can also put an end to those, with perhaps a few AI agents working on your behalf. Train these AI entities to respond to all spam and phone scams like an actual human. Have them respond to every obnoxious spam email, and engage any phone scammer with the appropriate responses to keep them on the phone.
These scams only persist because there are just enough little old ladies and just enough people who wishfully open spyware etc. The phone scammers that call me operate in a world where only their actual target people press “1” to hear about their auto warranty options. My guess is 99.9 percent of the people who get these calls hang up instantly or don’t pick up at all. This behavior actually is a benefit to the scammer, as it makes their operation more efficient. Think about it, they only want to spend their phone time & energy on potential victims.
There is an old saying in the sales world that a quick “no” from a contact is far better than spending an hour of your time on a dead end sale. But suppose the AI agents picked up every time and strung the scammer out. This would quickly become a very inefficient business for the scammer. Not to mention computing time is very inexpensive and AI technology is becoming standard. If everybody’s computer/iPhone in the world came with an AI application that would respond to all your nefarious emails and phone scams on your behalf, the scammers would give up at some point.
Those are my favorite two ideas security ideas for now. Let me know if you like either of these, or if you have any of your own out-of-the-box security ideas.
Share this: