Announcing the Next Generation NetEqualizer! The NE5000 is Now Available
The next generation NetEqualizer is here!
Introducing the NE5000 – our top-of-the-line powerhouse solution for larger organizations.

The NE5000 comes standard with bi-directional 10 Gbps fiber (40 Gbps fiber optional), and it can shape bandwidth for up to 50,000 concurrent users.
There are also a few exciting additions to the NE5000 not seen in previous models.
• First, we included built-in redundancy so that the device fails open.
• Second, we included built-in power redundancy as well so that the unit will never experience sudden outages.
• And third, we included a built-in management port to make network integration and management even easier.
Take a look at our price list for pricing information, or contact us if you have questions!

8.2 Release is Now Generally Available!
Our 8.2 Release is now generally available! This release includes two primary new features:
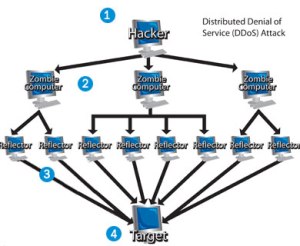
Distributed Denial of Service (DDoS) Monitoring
We are hearing that many of our customers need help with the onslaught of DDoS attacks on their networks. As the NetEqualizer is implemented near the network perimeter, and has visibility to all incoming and outgoing traffic, we are able to analyze traffic behavior and report on suspected DDoS attacks. Once identified as suspected DDoS, the NetEqualizer can then be used to block further traffic as needed.
IPv6 Bandwidth Shaping
For several years we have provided visibility to IPv6 traffic flowing through the NetEqualizer, to give you a view into how much IPv6 is on your network. We now feel that IPv6 has gained enough momentum to be a noticeable percentage on our customers’ networks. Therefore, as of 8.2 we are offering equalizing for IPv6 traffic. This will ensure that your full network gets the benefit of improved QoS during peak periods, for both IPv4 and IPv6 traffic.
—
The 8.2 update is simple and easy to install. We recommend upgrading as soon as possible in order to be properly prepared should a DDoS attack happen to you.
You can read more about these features in our release notes here. Our User Guide has also been updated with more information about how these features work.
These features are free to customers with valid NetEqualizer Software and Support who are running version 8.0+. If you are not current with NSS, contact us today!

Update on 2015 Tech Seminars and Conferences
Throughout 2015, we’ll be using our Newsletter to update you on Tech Seminars that NetEqualizer is hosting, as well as conferences we’ll be attending. Stay tuned!
Here is what we currently have planned for the near future:
NetEqualizer Tech Seminar
We are currently exploring sites for a Tech Seminar in the UK during the summer or fall 2015. As of this newsletter, nothing is  finalized. If you would like to host a tech seminar, we are also open to visiting a domestic site here in the U.S. or Canada, so please don’t hesitate to contact us.
finalized. If you would like to host a tech seminar, we are also open to visiting a domestic site here in the U.S. or Canada, so please don’t hesitate to contact us.
edACCESS Conference
edACCESS provides support and networking for information technology staff at secondary schools and small colleges. Most members come from schools with under 1,000 students.
We will be joining in the edACCESS conference at Mercersburg Academy on June 24, 2015 for Vendor Day! Feel free to stop by and pick up some NetEqualizer bling!
—
If you have questions on either the NetEqualizer Tech Seminar or the edACCESS conference, contact us!

8.3 Release (Expanded RTR) Arriving in Late Spring
Over the last few months we’ve continued to invest heavily in expanding our Real-Time Reporting (RTR) to make it even more robust. In late spring of this year, our 8.3 Release will be generally available.
The 8.3 Release includes many features our customers have asked for in the past to help improve their reporting experience. Here are just a few of the exciting new features:
Real-Time Pool and VLAN Dashboard
The current version of RTR has a real-time dashboard which shows current bandwidth usage. In Release 8.3, however, we’ve enhanced the dashboard to include both real-time pool and real-time VLAN bar graphs showing current usage. You can also easily see when your pools and/or VLANs are Equalizing.

Summary IP Reports
One of the most popular features in ntop, our previous reports offering, was the Summary Hosts Report, which highlighted how much bandwidth a particular IP address had used over a certain time period. In Release 8.3, we’ve added our own summary IP reports into RTR! Summary IP Reports is even better, as it will enable you to run custom database queries against all of the stored historical data to find exactly what you need. We will also include a handful of sample summary reports for common queries.

Historical Penalty Graphs
In Release 8.3, you’ll be able to see how the NetEqualizer has penalized traffic over time. RTR will now include graphs for tracking how many penalties are being enforced each minute. We’ll then store the data for up to four weeks. And, just like our other graphs, you’ll be able to export the data for retention if you so choose. This has been one of our most commonly requested features, and now it’s here!

—
Once 8.3 reaches GA, these features will be free to customers with valid NetEqualizer Software and Support who are running version 8.0+ If you are not current with NSS, contact us today!

Best Of The Blog
10 Things to Consider when Choosing a Bandwidth Shaper
By Art Reisman – CTO – APconnections
This article is intended as an objective guide for anyone trying to narrow down their options in the bandwidth controller market. Organizations today have a plethora of product options to choose from. To further complicate your choices, not only are there specialized bandwidth controllers, you’ll also find that most Firewall and Router products today contain some form of bandwidth shaping and QoS features.
What follows is an all-encompassing list of questions that will help you to quickly organize your priorities with regards to choosing a bandwidth shaper.
1) What is the Cost of Increasing your Bandwidth?
Although this question may be a bit obvious, it must be asked. We assume that anybody in the market for a bandwidth controller also has the option of increasing their bandwidth. The costs of purchasing and operating a bandwidth controller should ultimately be compared with the cost of increasing bandwidth on your network.
2) How much Savings should you expect from your Bandwidth Controller?
A good bandwidth controller in many situations can increase your carrying capacity by up to 50 percent. However, beware, some technologies designed to optimize your network can create labor overhead in maintenance hours. Labor costs with some solutions can far exceed the cost of adding bandwidth…








 commitment, and also want to spread out their costs over each month instead of incurring one upfront expense. If you have ever considered leasing a NetEqualizer, now is the time!
commitment, and also want to spread out their costs over each month instead of incurring one upfront expense. If you have ever considered leasing a NetEqualizer, now is the time!








 finalized. If you would like to host a tech seminar, we are also open to visiting a domestic site here in the U.S. or Canada, so please don’t hesitate to contact us.
finalized. If you would like to host a tech seminar, we are also open to visiting a domestic site here in the U.S. or Canada, so please don’t hesitate to contact us.









Application Shaping and Encryption on a Collision Course
March 18, 2015 — netequalizerArt Reisman, CTO APconnections
I have had a few conversations lately where I have mentioned that due to increased encryption, application shaping is really no longer viable. This statement without context evokes some quizzical stares and thus inspired me to expound.
Yes, there are still ways to censor traffic and web sites, but shaping it, as in allocating a fixed amount of bandwidth for a particular type of traffic, is becoming a thing of the past. And here is why.
First a quick primer in how application shaping works.
When an IP packet with data comes into the application shaper, the packet shaper opens the packet and looks inside. In the good old days the shaper would see the data inside the packet the same way it appeared in context on a web page. For example, when you loaded up the post that you are a reading now, the actual text is transported from the WordPress host server across the internet to you, broken up in a series of packets. The only difference between the text on the page and the text crossing the Internet would be that the text in the packets would be chopped up into segments (about 1500 characters per packet is typical).
Classifying traffic in a packet shaper requires intercepting packets in transport, and looking inside them for particular patterns that are associated with applications (such as YouTube, Netflix, Bittorrent, etc.). This is what is called the application pattern. The packet shaping appliance looks at the text inside the packets and attempts to identify unique sequences of characters, using a pattern matcher. Packet shaping companies, at least the good ones, spend millions of dollars a year keeping up with various patterns associated with ever-changing applications.
Perhaps you have used HTTPS, ssh. These are standard security features built into a growing number of websites. When you access a web page from a URL starting with HTTPS, that means this website is using encryption, and the text gets scrambled in a different way each time it is sent out. Since the scrambling is unique/different for every user accessing the site, there is no one set pattern, and so a shaper using application shaping cannot classify the traffic. Hence the old methods used by packet shapers are no longer viable.
Does this also mean that you cannot block a website with a Web Filter when HTTPS is used?
I deliberately posed this question to highlight the difference between filtering a site and using application shaping to classify traffic. A site cannot typically hide the originating URL, as the encryption will not begin until there is an initial handshake. A web filter blocks a site based on the URL, thus blocking technology is still viable to prevent access to a website. Once the initial URL is known, data transfer is often set up on another transport port, and there is no URL involved in the transfer. Thus the packet shaper has no idea of where the datastream came from, nor is there any pattern that can be discerned due to the encryption stream.
So the short answer is that you can block a website using a web filter, even when https is used. However, as we have seen, the same does not apply to shaping the traffic with an application shaper.
Share this: