By Art Reisman, CTO, http://www.netequalizer.com

Art Reisman
Editors note:
We often get asked where to find a simple network monitoring tool. Well, you can get more economical than this! All you need is some elbow grease and perseverance. Note: We are not the original authors of this idea and have adopted it to our blog, unfortunately I was unable to trace back to the original to give credit.
How to set up a computer for network monitoring – All for free!
This is not as hard as it looks, once you have done it a time or two you can be up and running in less than 5 minutes, assuming you have high-speed access to the Internet.
Do you have a computer with the following?
- 2 network cards installed or two on-board LAN ports
- 1 CDRom drive
- 256 to 1,024 or more Meg of RAM
- monitor
- keyboard
- mouse (optional — it is necessary if you boot into the graphics mode, though)
If so, you can be minutes away from having a network monitoring machine up and running that you can insert in your network and see what is going on. If you follow these instructions it will act as a transparent bridge so no other machines or routers will know the difference.
The Knoppix CD is a live CD distribution which does not need a floppy or hard drive to run. It is all self contained on the CD. It uses your RAM as a read/writeable area so you can still install a few programs if need be and edit most of the configuration files.
You can get the Knoppix iso image from http://knopper.net/knoppix/ or the English version at http://knopper.net/knoppix/index-en.html
The download page for English reading when this article was written is at http://knopper.net/knoppix-mirrors/index-en.html
Download a CD image of 4.02 or better. A typical file name will be:
KNOPPIX_V4.0.2CD-2005-09-23-EN.iso
The filename ends in -EN and if you speak english then get that one. If you speak German, then get the -DE one.
Now burn that .iso file to a CD using your program of choice (burning the CD image to make a bootable CDRom is not covered here).
You should insert your machine into the network so it is between the Router and the switch, assuming you want to monitor traffic going from or to your network and the Internet. You may have to use a crossover cable from one of your machines LAN ports to the router and a standard network cable from the other LAN port on your machine and the switch.
Internet or Router or ???
_________
| |
| | eth0
_____| |_______________________
| Monitoring Unit |
|_____________________________|
||
eth1 ||
_______________________||______
| Internal Network Switch |
|_______________________________|
|| || || || || || || || || || ||
Your internal network users or whatever you want to monitor
Once that is done you can run Knoppix by placing it into your machine and booting up. If you have a limited video card or an old monitor then you can hit the appropriate key when Knoppix boots up and find the option to boot into text mode only. You may also want to do this if you have limited RAM.
Once you are booted up and running Knoppix you can do the following:
If you booted to an XWindows look then click on the little computer screen icon next to the house on the bottom tool bar. If you booted into text mode you do not have to do that.
Now gain root access by typing the following and then Enter:
su
Now that you are root you can run the following commands to start up your transparent bridge and get traffic flowing through the machine from one lan port to the other. The IP 192.168.1.153 below was use as an example along with the default gateway being 192.168.1.1 so change those if your network is on a different IP range. You will want to give it an IP so that you can get into the machine from another machine on the network. In some cases you might want to be able to get to it from the Internet so in that case you would have to give it an IP that can be reached from the Internet and not a 10.x.x.x or 192.168.x.x number.
ifconfig br0 down
brctl delbr br0
ifconfig eth1 down
ifconfig eth0 down
ifconfig eth0 promisc 0.0.0.0 up
ifconfig eth1 promisc 0.0.0.0 up
brctl addbr br0
brctl addif br0 eth0
brctl addif br0 eth1
ifconfig br0 192.168.1.153 netmask 255.255.255.0 up
route add default gw 192.168.1.1
It may take a half a minute for traffic to start flowing through the transparent bridge br0.
Once you can do something like:
ping http://www.yahoo.com
and it comes back with ping times then you are ready to continue. BTW: hit CTRL C to stop ping.
apt-get update
apt-get install ntop
Say Y or hit enter to install ntop. When it is all done do the following:
mkdir /var/log/ntop/rrd
chmod -R 777 /var/lib/ntop
chmod -R 777 /var/log/ntop
warning: the chmod commands above allow anyone to read/write to those directories that can get to the machine so keep your machine safe with firewalls or passwords accordingly.
You can now run ntop. You need to run ntop from the console or via SSH first by just running the command:
ntop
It will ask you for an admin password and then again to,verify it. This is for the admin interface in ntop.
Once ntop is up and running in a window you can leave that up and just go to your web browser and put in the URL of:
http://192.168.1.153:3000/
The :3000 is the special port that the ntop web server runs on.
If you choose the menu item Summary and then Network Load you should see a graph of your traffic. Not all ntop menu items are used on every system. Most of the time you will only be using the items under Summary or All Protocols.
You now have a running bandwidth monitoring system. ntop is the only application mentioned here but there are others installed on the default Knoppix CD already too.
Related post
The systems I have installed this routine on vary from a system with a Celeron to one with a P4 CPU Running on 10/100 Realtek chipsets to 10/100/1000 Intel chipsets. From 256 Meg of RAM to 2 GIG. Knoppix runs very well on a variety of hardware but your mileage may differ.
Created by APconnections, the NetEqualizer is a plug-and-play bandwidth control and WAN/Internet optimization appliance that is flexible and scalable. When the network is congested, NetEqualizer’s unique “behavior shaping” technology dynamically and automatically gives priority to latency sensitive applications, such as VoIP and email. Click here for a full price list.


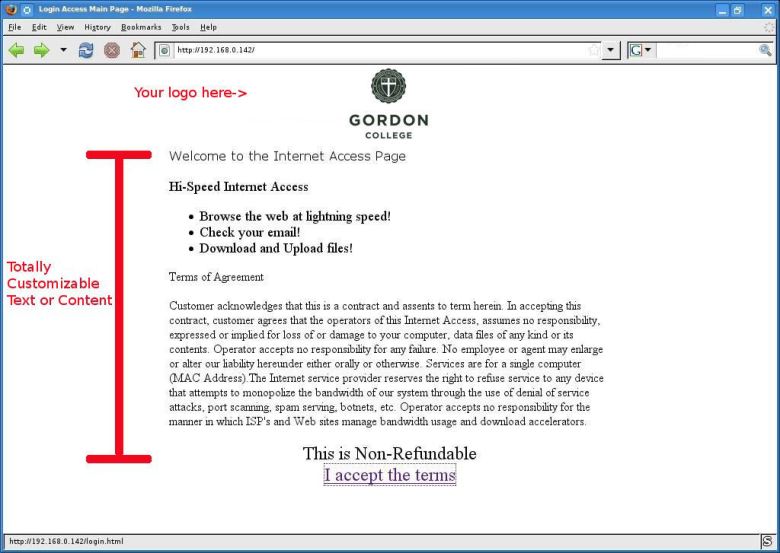
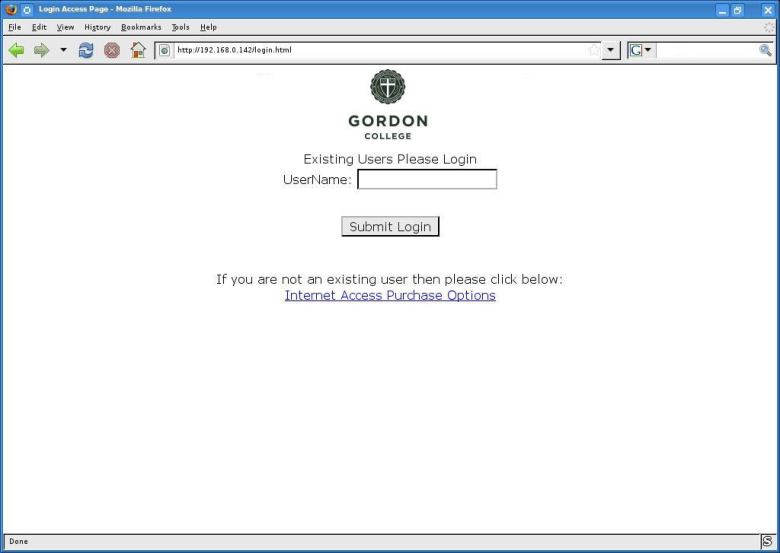
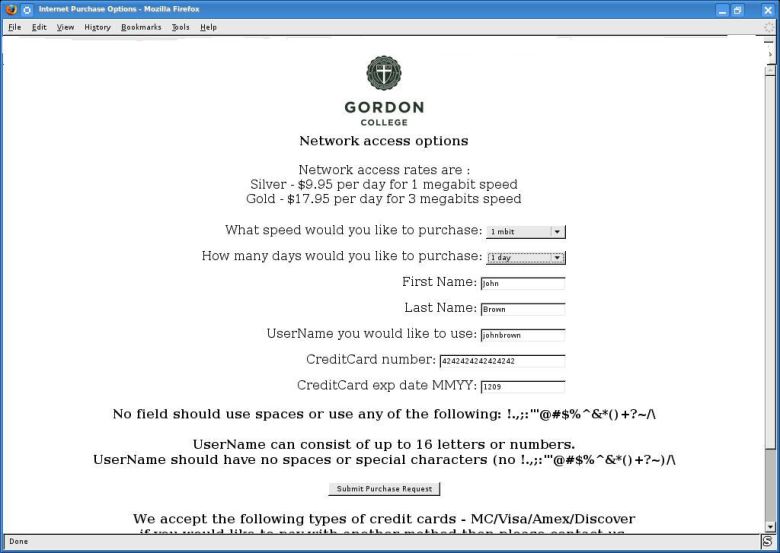
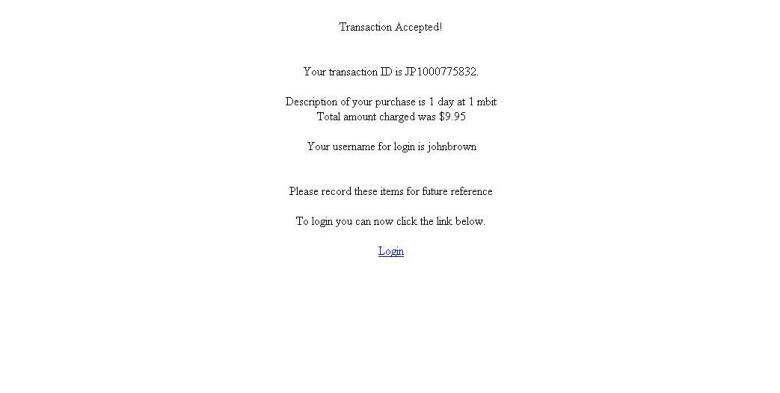




Obama’s Revival of Net Neutrality Revisits An Issue Hardly Forgotten
June 1, 2009 — netequalizerLast Friday, President Obama reinvigorated (for many people, at least) the debate over net neutrality during a speech from the White House on cybersecurity. The president made it clear that users’ privacy and net neutrality would not be threatened under the guise of cybersecurity measures. President Obama stated:
“Let me also be clear about what we will not do. Our pursuit of cyber-security will not — I repeat, will not include — monitoring private sector networks or Internet traffic. We will preserve and protect the personal privacy and civil liberties that we cherish as Americans. Indeed, I remain firmly committed to net neutrality so we can keep the Internet as it should be — open and free.”
While this is certainly an important issue on the security front, for many ISPs and networks administrators, it didn’t take the president’s comments to put user privacy or net neutrality back in the spotlight. In may cases, ISPs and network administrators constantly must walk the fine line between net neutrality, user privacy, and ultimately the well being of their own networks, something that can be compromised on a number of fronts (security, bandwidth, economics, etc.).
Therefore, despite the president’s on-going commitment to net neturality, the issue will continue to be debated and remain at the forefront of the minds of ISPs, administrators, and many users. Over the past few years, we at NetEqualizer have been working to provide a compromise for these interested parties, ensuring network quality and neutrality while protecting the privacy of users. It will be interesting to see how this debate plays out, and what it will mean for policy, as the philosophy of network neutrality continues to be challenged — both by individuals and network demands.
Further Reading
Share this: