8.4 Release Update
User Interface Enhancements
We have exciting news to share regarding our next software update – Release 8.4. Throughout 2015, we made big changes to our Real-Time Reporting (RTR) and implemented tons of useful features. In 2016, we’ll be focusing our efforts on the rest of the NetEqualizer User Interface. Here are just a few of the things you can expect:
1) Better Configuration Management
We’ve listened to your feedback and are adding in the ability to edit traffic limits and other rules without removing them, control the units (Bps, Kbps, Mbps, etc.) displayed throughout the NetEqualizer interfaces, and manage the configuration all in one place – just to name a few!
2) Secure Logout and HTTPS by default
These popular feature requests will now be standard on all units running the 8.4 Release. Users will now be able to log out from the user interface securely and all data will be sent over HTTPS to and from the NetEqualizer.
3) Manage Time and Date from the GUI
With the 8.4 Release, you’ll be able to manage all time and date features of the NetEqualizer from the user interface instead of the command line.
4) Named Pools
This is one of the most requested items and it will be a reality in the 8.4 Release. With this release, you will be able to name your Pools however you see fit.
Our time frame for General Acceptance of this release is March or April of 2016.
As with all software releases, the 8.4 Release will be free to all customers with valid NetEqualizer Software and Support (NSS).

What Our College Customers Are Saying…
Last month, we featured Morrisville State College in New York, our newest Case Study. Since then, we have heard from several more colleges who wanted to offer their feedback.
Please contact us if you would like your quote added to our testimonials page, even if you are not in the higher education space! We love hearing from all our customers about how we’ve helped them control congestion on their networks.

You can view all of the College & University Testimonials on our website. Here are our two most recent:

United States Naval Academy
IT Administration – United States Naval Academy
“Faced with mounting costs of upgrades for maintenance on our existing bandwidth shaper, in 2014 we did a little research and decided to try the NetEqualizer. We are currently running 1 gigabit for the entire campus, including students and faculty. Our bandwidth utilization is maxed out for most of the day and into the evening. Without a solid bandwidth shaper in place, operations would come to crawl.
Since deploying the NetEqualizer in the Spring of 2015 we have pretty much forgotten about it (in a good way). The NetEqualizer allows us to run at full capacity without the hassles of making adjustments on a daily basis.
One of the best investments we have ever made.”

Delaware Valley University
Michael Davis – Executive Director of Technology Services
“Delaware Valley University shifted from a packet shaping tool to a NetEqualizer over a year ago, and it is one of the best infrastructure decisions we have made.
The NetEqualizer has allowed us to provide better service to our students without increasing bandwidth, and we hear fewer complaints than ever about bandwidth.
We are planning our next bandwidth increase, and the NetEqualizer is going to make this better than usual. Factoring in student satisfaction with the amount of time that we no longer have to spend tuning a packet shaping device has made us very happy customers.
The support and sales teams at NetEqualizer are also fantastic.”
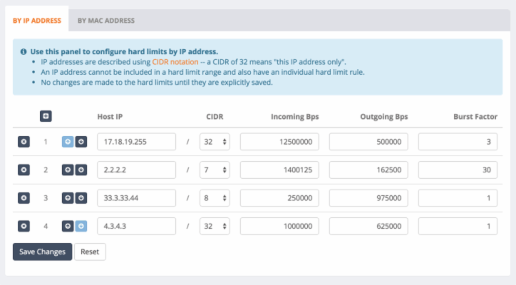
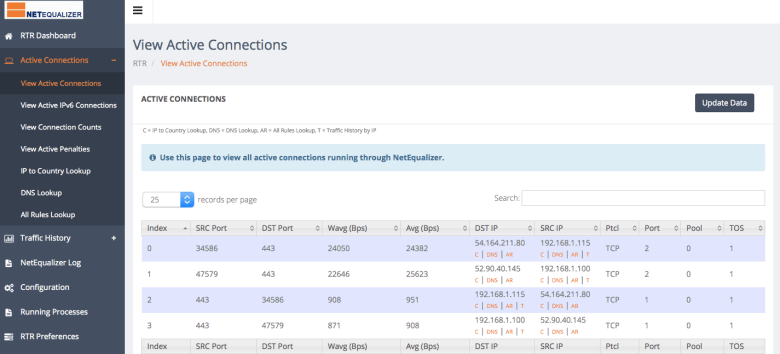
How Can RTR Help You?
Check Out RTR Best Practices (Part 2)
RTR is great as a simple reporting tool, but it can also be much more! Below we share some helpful ways to utilize the different reports in RTR to better configure your NetEqualizer and understand your network. This is Part 2 of a two-part series – read about Part 1 last month!
1) Figure out who has used the most data over time
Usually on the NetEqualizer, we are talking about usage rates like Mbps, Kbps, etc. But, sometimes you might want to know who has downloaded or uploaded the most data over time (in MB, GB, etc.). Use Traffic History -> Top Talkers to find out!

2) Use the Start/Stop RTR page to view system status messages
The NetEqualizer has processes in place that will rotate old data and keep you from running out of memory. However, you can check to make sure things look good and RTR is running smoothly on the Start/Stop RTR page.

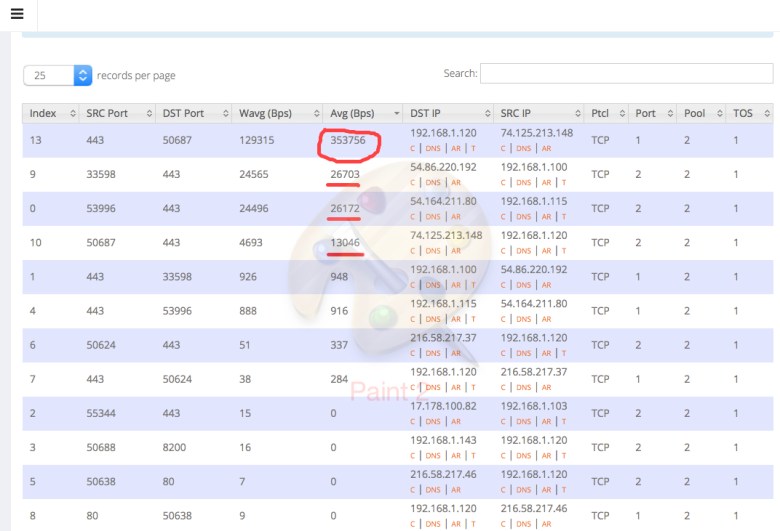
3) Use the General Penalty Reports page to correlate data to the General Traffic History page
In last month’s newsletter, we showed a perfect example of what we’d expect a network to look like. Check out the graphs for Morrisville State College in their Case Study.
We always want to ensure that some Equalizing is occurring during busy times. If you don’t see many penalties during busy times, your HOGMIN value may be set too high.
Consult the User Guide for appropriate HOGMIN values for your network.


If you are current on NetEqualizer Software and Support (NSS), and have a question about RTR or would like a walk through, click the button below!

It Is Not Too Late… To Give Input Into The 2016 Roadmap
For those of you that have already responded, THANK YOU. Rest assured that we have collected your feedback and added it to our Feature Request List for 2016.
If you have not yet responded, there is still time to influence our fall/winter 2016 release.
If you have a great idea for us, please let us know!
No idea is too “out there” – we want to solve your crunchiest, toughest networking issues.
Email us your idea.
Best Of The Blog
Regulate DDoS Like Pollution
By Art Reisman – CTO – APconnections
I just read another article on DDOS attacks and how companies are being extorted. As usual I am thinking way out of the box again.
Background on the mechanics of DDOS attack
The raw tools of a DDOS attacker are made possible by the billions of computing devices sitting around the world attached to the Internet. A DDOS attacker probes constantly for computers to hack, and then once they have access to several hundred or more in their control, they can point them to any business, sending a storm of data requests jamming Internet links from the outside. Think of a million people trying to cram into the door of your apartment all at once, you would be trapped inside…

 by mitigating his customers’ bottlenecks. Contact us if you are interested in more details.
by mitigating his customers’ bottlenecks. Contact us if you are interested in more details.






























IT/Tech Geek New Year Resolutions
December 31, 2015 — netequalizerHere are my tech geek new year resolutions for 2016. If you have a loved one or friends that could use some help breaking away from their tech induced coma please share.
In 2016 I resolve to:
Share this: